How Token Protection in Entra Secures BYOD for AVD and Windows 365 (or does it?)
In 2024, Microsoft detected 147,000 token attacks, a 111% increase from 2023!

Table of Contents
- Introduction
- The Silent Threat: What is Token Theft and Why Does It Matter?
- How Entra ID Conditional Access Mitigates Token Theft
- A Look at Licensing Requirements
- Token Theft Protection for the Budget-Conscious
- Now Supporting Token Theft Protection: The Windows App
- Configuring Token Protection in Entra ID
- Token Protection: Support, Limitations and What To Watch Out For
- Final Thoughts
TL;DR
- Updated July 2025: Token Protection for AVD and Windows 365 now only requires Entra ID Plan 1 reducing the licensing barrier and expanding adoption.
- Token Protection binds sessions to devices to stop stolen tokens being reused on unmanaged or BYOD endpoints.
- The Windows App is now supported, making this a critical update for AVD and Windows 365 environments using the modern client.
- Business Premium includes everything you need to enable Token Protection without jumping to enterprise-level pricing.
- Practical risk-reduction tips included for organisations not yet ready to deploy Token Protection or lacking full Conditional Access maturity.
Introduction
Securing virtual desktop environments is more important than ever, especially with the rise of bring-your-own-device (BYOD) and remote access. Token theft has become a growing concern in AVD and Windows 365 deployments.
Microsoft has taken a significant step forward by extending Token Protection in Entra Conditional Access to support the Windows App, now the primary client for accessing both AVD and Windows 365. It marks a significant step forward in securing sessions on devices that IT does not manage, and it shows that Microsoft is continuing to invest heavily in the Windows App.
In this post, I'll walk through what token theft is, how Token Protection works, and why this update matters for organisations using BYOD and personal devices, including those in the non-profit space.
Let’s jump in! 🥷
The Silent Threat: What is Token Theft and Why Does It Matter?
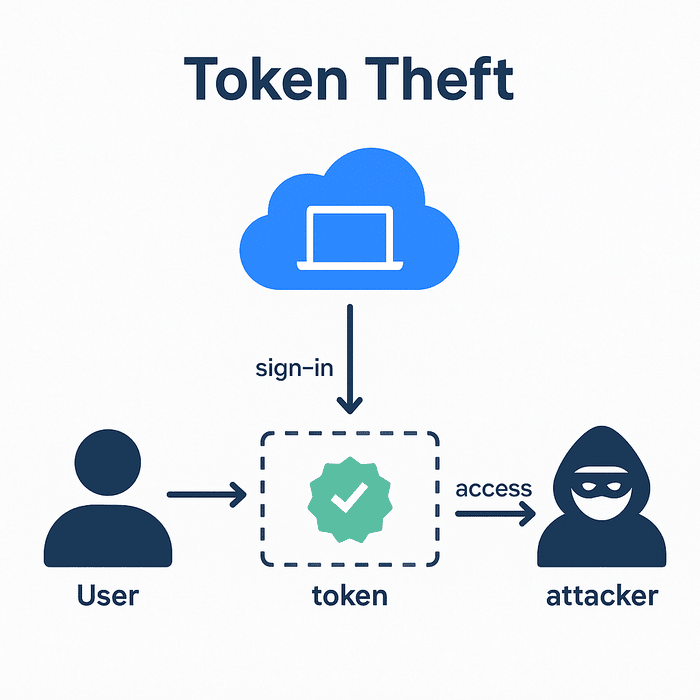
Token Theft is one of the most prevalent threats in identity-based security. When a user signs in, authentication tokens are issued and stored on the device to maintain session access. These tokens allow the user to access cloud services like Microsoft 365, Azure Virtual Desktop, and Windows 365 without needing to sign-in again each time.
The problem is that these tokens can be copied from the device and used elsewhere. If an attacker steals a token, they can bypass multi-factor authentication and any conditional access policies in place. To Microsoft, the session still appears valid because the token itself is legitimate, even if it is now being used by someone else, in a completely different location, on a completely different device!
This type of attack is difficult to detect and even harder to stop, particularly in BYOD and unmanaged device environments (think non-profits) where IT teams lack visibility or control over the device.
What makes token theft especially dangerous is that it doesn't require sophisticated malware. If a non-technical client relationship team can demonstrate token theft in a basic webinar, then attackers are already several steps ahead.
How Entra ID Conditional Access Mitigates Token Theft
Microsoft Entra ID Conditional Access is now the frontline of identity security. It checks a range of signals like user identity, device compliance, location and risk level, then decides whether access is allowed, blocked or requires further verification.
But there has been a gap!
Even with Conditional Access in-place, attackers can steal authentication tokens from a legitimate session and reuse it on another device. The result? Access Granted, without triggering any alerts. Conditional Access would trust the session because the token itself is valid.
Enter Token Protection
Token Protection changes the game. It binds the token to both the user and the original device it was issued on.
If someone tries to use that token on an application from a different device, even with the correct credentials, access is denied. This directly addresses the silent threat of token theft and cuts off a common method used in post-authentication attacks.
Why It Matters For Bring-Your-Own-Device (BYOD)
In BYOD scenarios, especially where devices are not managed by IT, control is limited. Organisations, customers or non-profits might not own the device, but with Token Protection in place, you can still control how the session token behaves.
This is a major win for industries that rely on personal devices such as non-profits, education and charity organisations. Another common BYOD scenario which can be easily forgotten about is contractors.
A Look at Licensing Requirements
To enable Token Protection in Microsoft Entra ID, organisations now only need Microsoft Entra ID Premium P1. This license provides the advanced identity governance and protection features that Token Protection relies on. This is also included in Business Premium licenses which most SMBs will already be on!
Business Premium licensing is approx. £17 per user per month.
If your organisation already uses capabilities like Identity Protection, risk-based policies and Privileged Identity Management (PIM); you're likely licensed for P2!
Who Should Consider Business Premium?
- Organisations aiming to strengthen session security using token binding with Built in Entra ID P1.
- With built-in support for managing both company-owned and personal devices, Business Premium is perfect for SMBs embracing remote work or dealing with contractors.
- Environments with a focus on zero-trust and risk-based access decisions.
- Instead of piecing together separate security and identity tools, Business Premium bundles them in one license at around £17 per user per month. Ideal for SMBs looking to simplify stack and billing.
Entra ID P2 is available as a standalone license, or as part of the E5 Enterprise license. Depending on the use-case, there are different licensing paths that can be taken.
Token Theft Protection for the Budget-Conscious
For SMBs, non-profits and organisations that cannot justify the cost of Entra ID P2, there is some good news. If you are already using Conditional Access, you can take meaningful steps to reduce the risk of token theft. These measures do not fully prevent it, but they can significantly lower your exposure.
Here are some practical controls you can implement. Whilst some of these depend on how your customers/organisations operate, they go a long way in mitigating risk.
Recommended Controls
- Block legacy authentication protocols
Disable outdated authentication methods that can bypass Conditional Access entirely. - Block unused device platforms
If your users do not use certain platforms, block them at the Conditional Access level:
- Linux
- macOS
- Windows
- Windows Phone
- Apply geographic restrictions
Only allow sign-ins from expected regions, such as:
- United Kingdom
- Restrict Entra ID device registration
Limit registration to trusted IP ranges or require MFA for registration. And, consider whether users are allowed to register BYOD devices to Entra ID. - Require compliant devices
Only allow access to Microsoft 365 apps and data from:
- Entra ID joined
- Compliant or hybrid-joined devices
- Disable persistent browser sessions
Especially important when users are accessing services from personal or shared BYOD devices. - Block device code flow
Prevent a common method used in phishing-based token theft.
Want some help getting these policies in-place, or have some questions? Get in touch!
Now Supporting Token Theft Protection: The Windows App
This is the game-changer. Microsoft has expanded Token Protection to include the Windows App, increasing security for users accessing Azure Virtual Desktop and Windows 365 through the Windows App.
With this update, authentication tokens are now securely tied to both the user and the specific device they were issued on. This means that even if a token is intercepted, it cannot be used on another device, effectively mitigating the risk of token theft.
Key Benefits
- Enhanced Security with tokens bound to the original device, preventing unauthorised use elsewhere.
- Seamless Integration now working with the Windows App, the new, primary app for AVD and Windows 365.
- Improved Compliance aligning to zero-trust principles by ensuring only trusted devices can access your virtual desktop environments.
This development is particularly beneficial for organisations utilising BYOD or unmanaged devices, as it provides an additional layer of security without compromising user experience.
Configuring Token Protection in Entra ID for AVD
Here are some brief steps on how to create a new policy, focussed on token theft protection. Video walkthrough can be found below the guide!
- Log into Entra ID, navigate to Conditional Access and then select Policies.
- Select New Policy, name the policy aligned to your naming conventions.
- Under assignments, you're likely to include all users who are licensed with Entra ID Plan 1, either via a standalone license or through Microsoft 365 subscriptions such as Business Premium.
- Make sure you exclude your emergency-access accounts; but ensure other admin accounts are included.
- Find Target Resources, select Resources, select Include, and select the following resources:
- Azure Virtual Desktop
- Windows 365
- Windows Cloud Login.
- Now, under Conditions, find Device Platforms, set configure to Yes, and make sure Windows is included.
- Under Client Apps, set Configure to Yes, and ensure only Mobile Apps and Desktop Clients are enabled.
- Navigate to Access Controls, Session, and select Require Token Protection for Sign-In Sessions.
- Confirm settings, enable in report-only mode, assess impact.
- Select Create to create the policy.
Token Protection: Support, Limitations and What To Watch Out For
Before deploying Token Protection, it is essential to understand the support configurations, known limitations, and key design considerations.
As this is in preview, Microsoft will continue to improve support, but there are lots of design gaps. Some of the documentation is also unclear - with what is and what isn't supported. And it would be much too detailed to tabulate it here. There is a table below, but please refer to the Microsoft article for up to date changes.
Final Thoughts
Token Protection works best with native applications like the Windows App, Outlook and Teams. It doesn't apply to web browsers. It's important to understand where Token Protection adds value and just as crucial to know where it does not.
This feature helps reduce the risk from post-authentication, but the current lack of browser coverage leaves a noticeable gap. Token protection is still in preview, and in my view, this limitation needs to be addressed for the technology to reach its full potential.
That said, Microsoft are clearly moving in the right direction. And if anything changes around the browser-based support for token theft, I'll update this blog post to reflect it.
Until then, weigh your risks, review your licensing and apply the right controls that make sense for your environment and budget. If you need guidance on where to start, or how to apply these protections, reach out via LinkedIn!

Comments ()